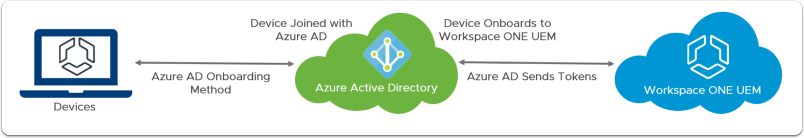
In some scenarios, especially for new companies there is no on-premise infrastructure and organisation wouldn’t be investing money to go this route. Instead they will be utilising cloud solutions which are currently available, like Microsoft Azure. One of the main services that are being used within organisation which have on-premise infrastructure is Active Directory. This is also available in Azure in a service called Azure Active Directory (AAD). However, integration between AAD and WS1 doesn’t work in the same way as with on-premise AD and requires SAML integration, rather then standard LDAP configuration. In this post I will describe how to do that.
In order to be able to enroll devices using users in AAD follow below steps to complete integration between two platforms.
Add Azure application
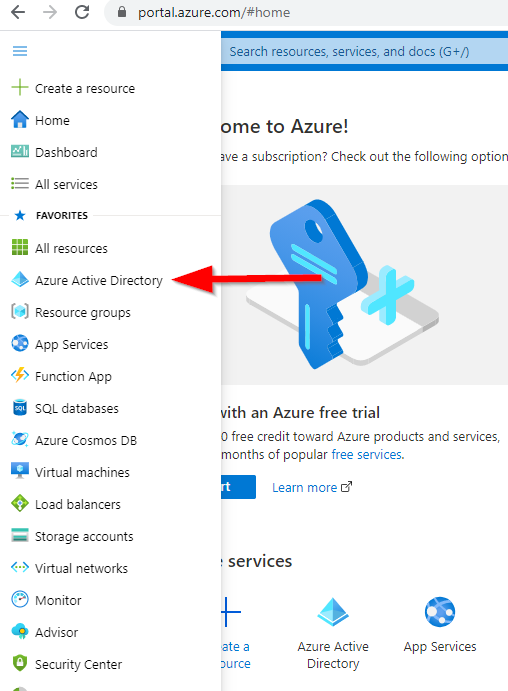
Navigate to https://portal.azure.com and login to your tenant. Then follow below steps:
- Select AAD service
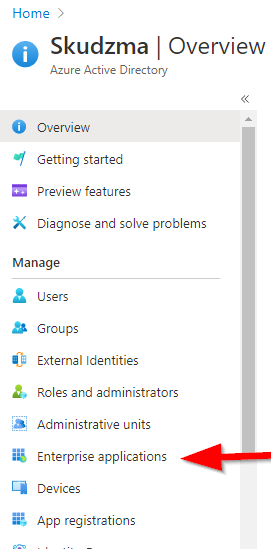
- Select Enterprise applications.
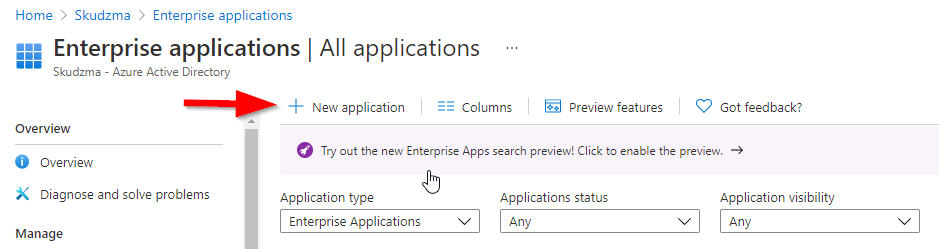
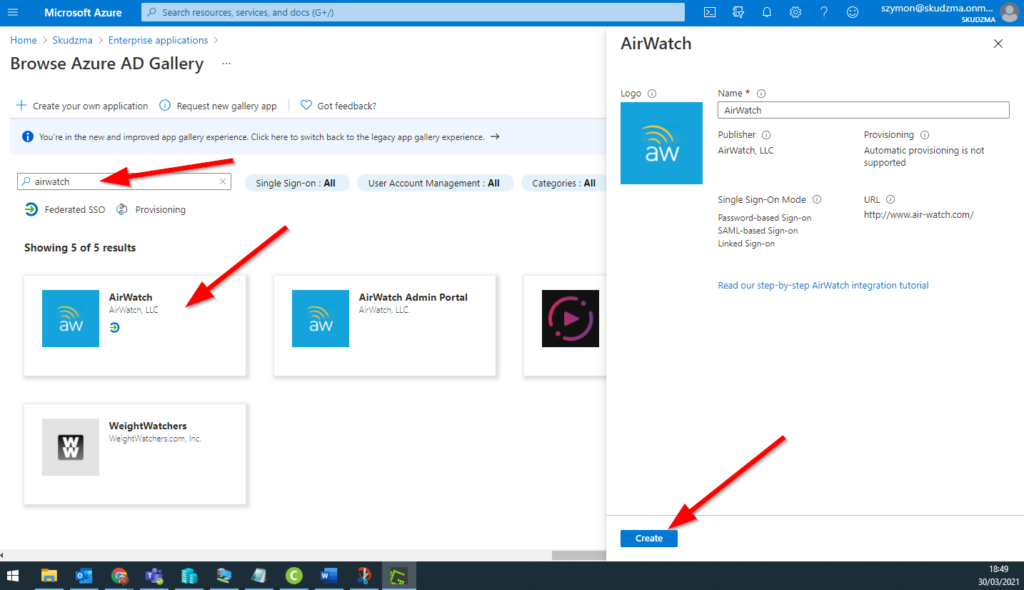
- Within Enterprise application section click new application
- Search for AirWatch and then select Create
Configure AAD Application
Once application is added administrator needs to configure Single Sign-On and enable SAML authentication for that enterprise app.
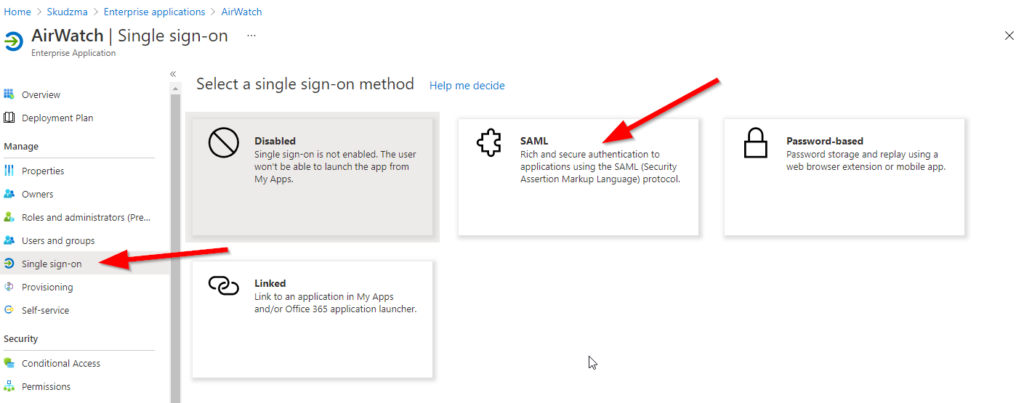
On next page, scroll down to point 3 and select “Download” next to Federation Metadata XML. This will download xml file which we would use in WS1 console.
Configure WS1 Directory Settings
Now, leave this page open and open new tab/window and login to WS1 console. Navigate to Settings => System => Enterprise Integration => Directory Services.
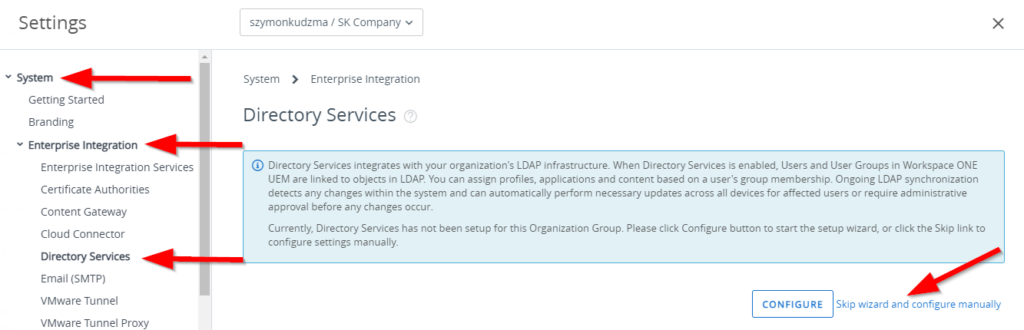
Skip the Wizard option and configure directory services as below:
- Directory type – set to none
- Use SAML for Authentication – Enable
- Enable SAML Authentication For – check required options (in our case I have selected enrollment and self-service portal only)
- Use New SAML Authentication Endpoint – Enable
- Import Identity provider settings – upload xml file downloaded earlier from Azure portal.
- Press Save at the bottom of the page (note: settings will not be uploaded until save is completed)
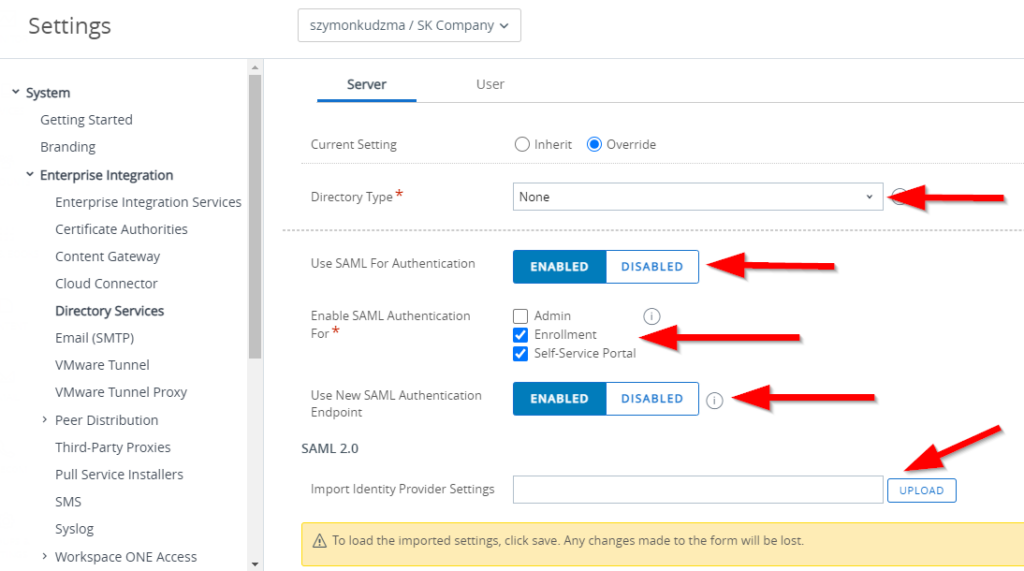
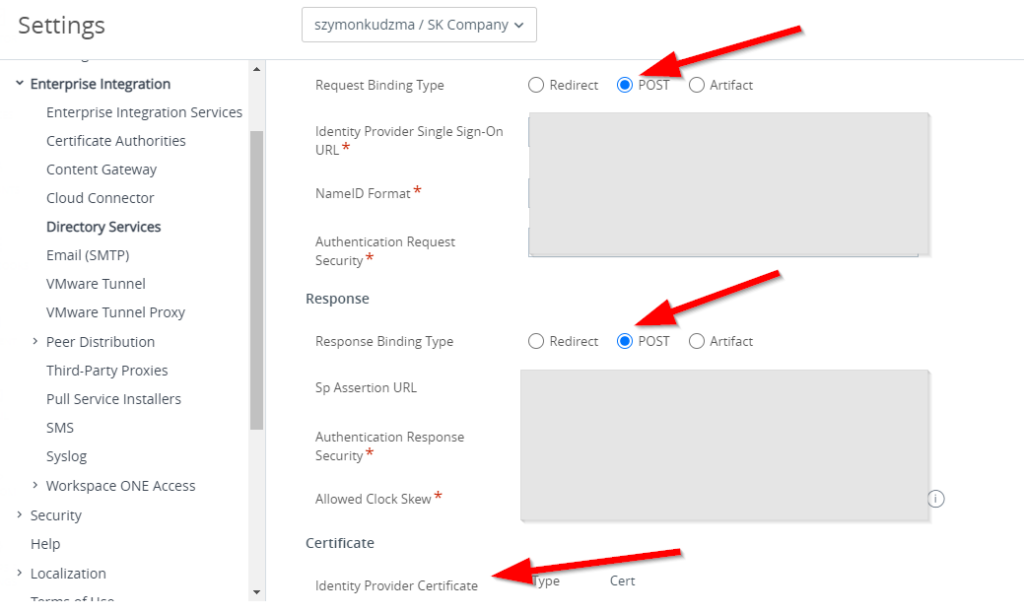
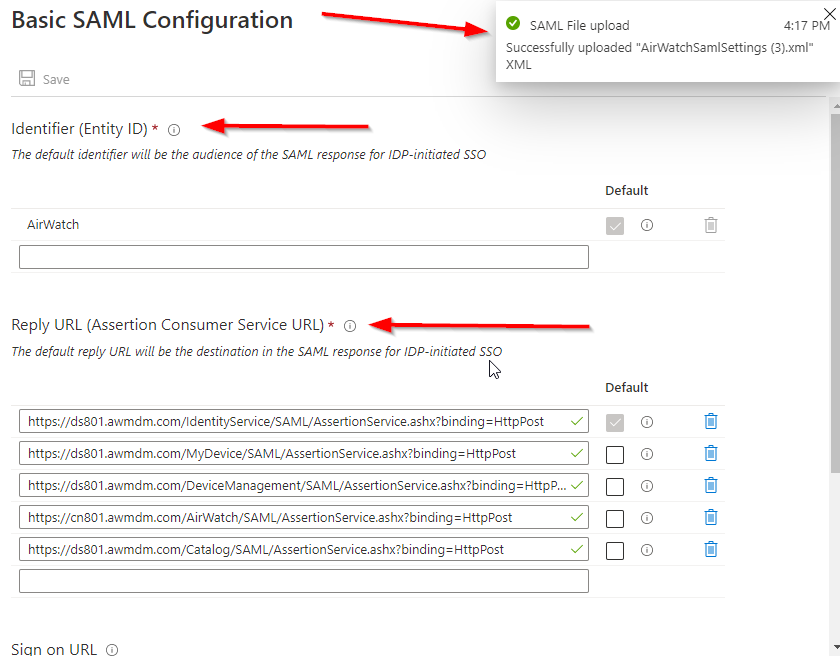
Once save is completed, please make sure that all values and certificated is populated, as well as Request and Response binding type is set to “Post”
Next go to the user tab and Edit below configuration:
- Base DN field to “WAAD”
- Object Identifier to http://schemas.microsoft.com/identity/claims/objectidentifier
- Username to http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
- Display Name to http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname
- First Name to http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname
- Last Name to http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname
- Email to http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
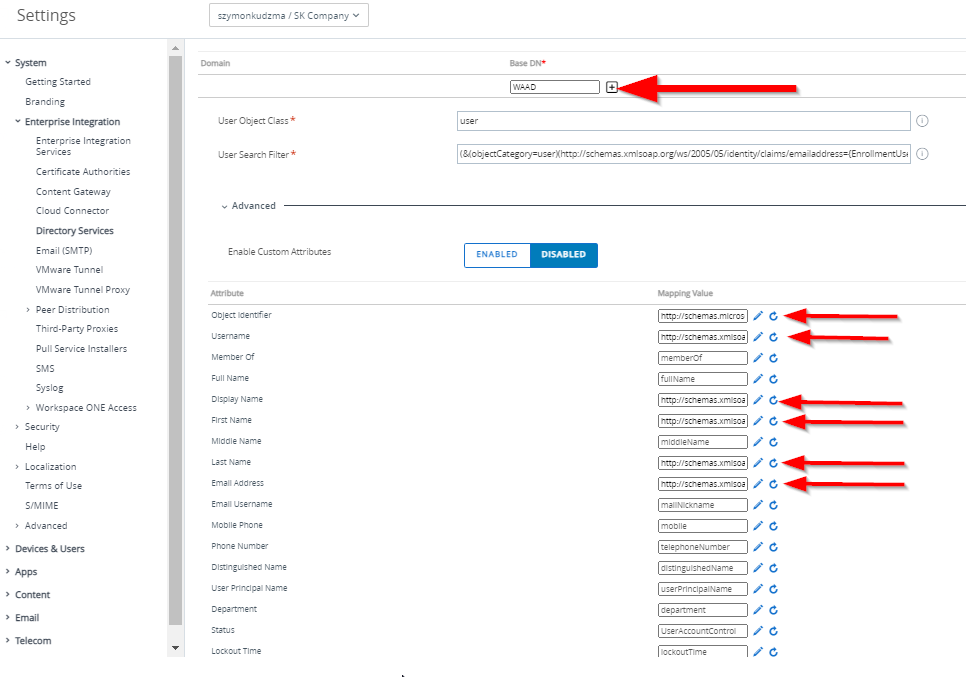
Note: In order to edit the field, click the pencil icon. You will be then able to edit the field, but no visual change will be presented.
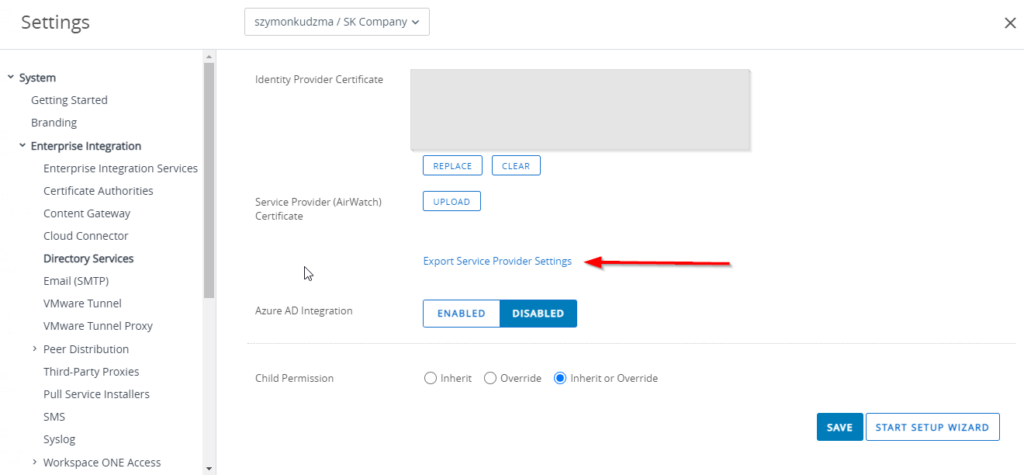
Once all required fields are completed, click save and go back to the server tab. Scroll down to the bottom of the page and click on Export Service provider Settings. An XML file will be downloaded which we can then import into Azure.
Complete configuration of AAD Application
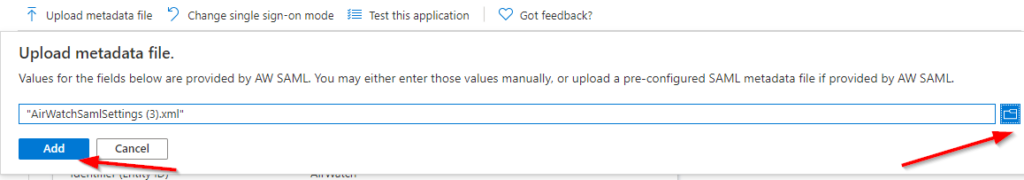
Navigate back to open tab/window within Azure Portal and enterprise application SSO configuration setting. Click on upload metadata file, select an xml file downloaded earlier from WS1 and click Add. This will populate all required fields based on WS1 configuration. Once all settings are uploaded successfully, “SAML file upload” message with green check box will be presented
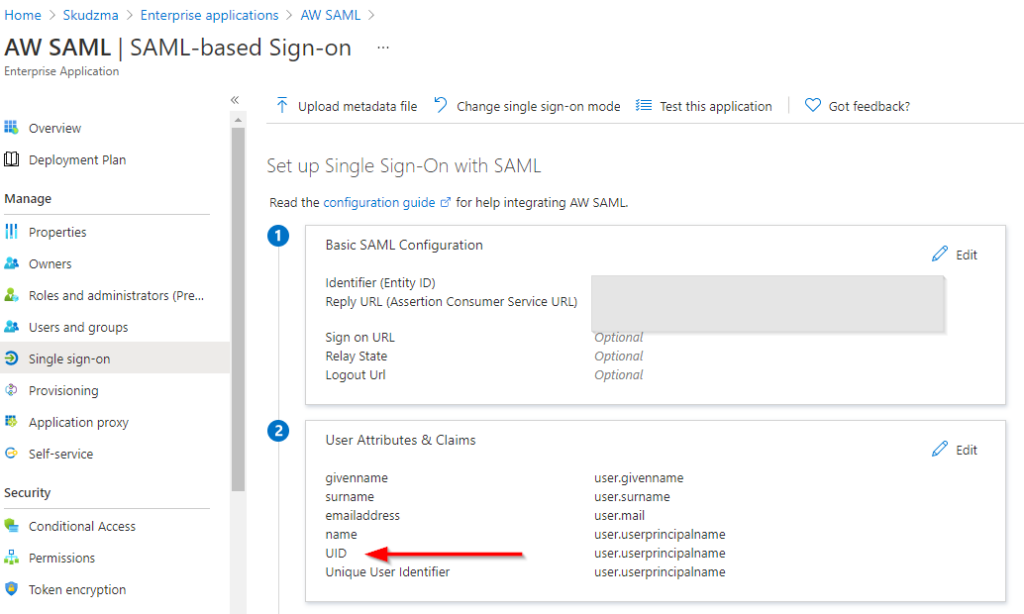
Note: If you would try to add enterprise application manually, rather then Airwatch from the list, “UID” filed will be missing in point 2. If this is the case select edit and add the new claim as per below:
UID = user.userprincipalname
Configuration is now completed and you should be able to enroll a device using AAD user.


Es un buen blog, gracias por tu ayuda.
Thank you!
¡Hola! Alguien de mi grupo de Facebook compartió este sitio con nosotros, así que vine a echarle un vistazo. Definitivamente estoy disfrutando la información. ¡Estoy marcando marcadores y lo estaré tuiteando a mis seguidores! Gran blog y diseño maravilloso.
Thank you!